Overview
Features
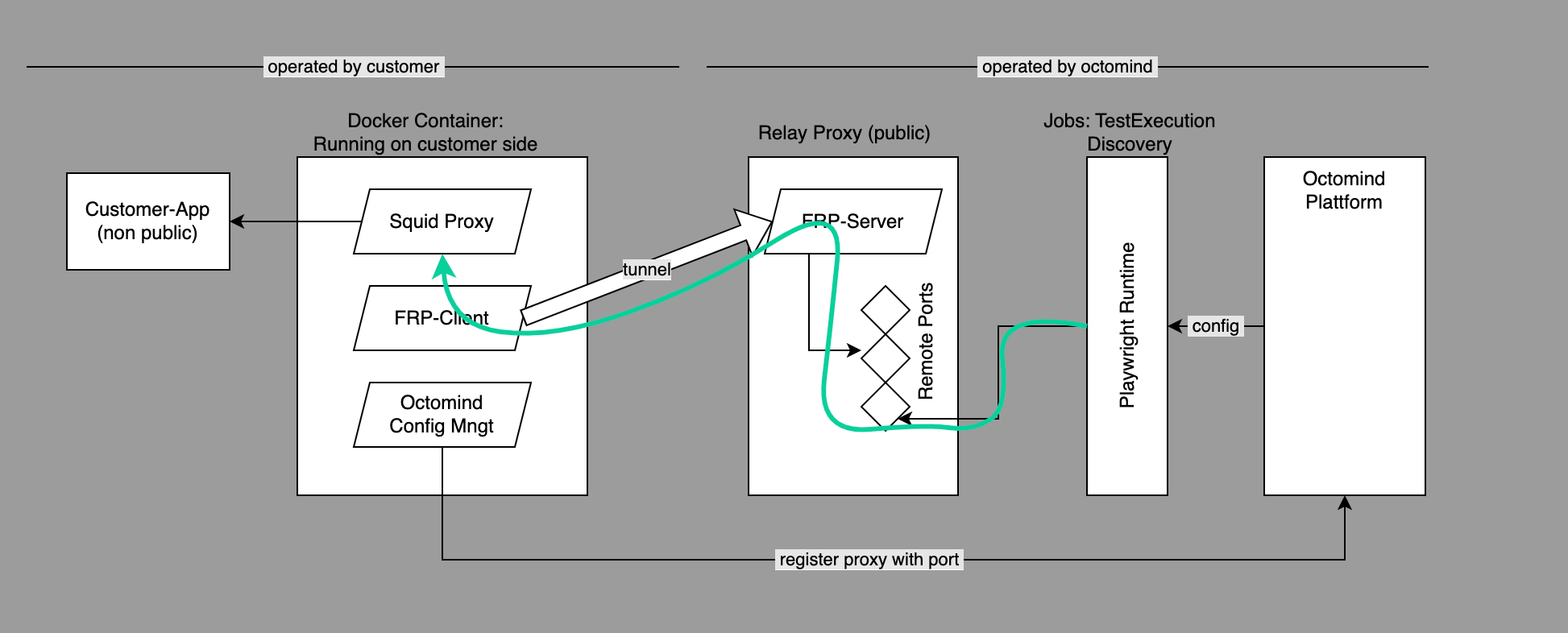
Tunneling with FRP
The tunneling is managed using FRP, connecting the worker’s frp-client to Octomind’s proxy servers (EU or US). It requires access permission to specific public IPs:35.192.162.70, 34.159.153.198 or 34.129.193.156.
Access to private web applications
The embedded Squid proxy server allows requests from the private network, mimicking public proxy requests from within the customer’s network.Test execution and generation
After registering the worker with Octomind, users can configure the proxy location for executing generation or test runs.Usage
Customer can run and build the private location worker on their premises using a container. Container image will be provided by Octomind, see registry, or it can be built on your own. See below to run the container a few environment variables are needed.Environment vars
- APIKEY: the octomind APIKEY for your organization
- PLW_NAME: name of the private locations worker as registered in the octomind platform (name must match)
- PROXY_USER: username for the (squid) proxy
- PROXY_PASS: password for the (squid) proxy
- SERVER_ADDR: the address of the server that the worker will connect (default:
35.159.153.198)
Currently, only one instance of the worker is supported. We will support
multiple instances of the worker with the same name as we scale.
Run
Private location worker can simply run as docker container:Security considerations
- The container image is open-source, allowing customers to review and build their own versions. Check out its GitHub repo.
- Network access can be restricted to the tunnel server and test targets.
- The Squid proxy requires authentication, ensuring secure access. Username and password is controlled by the customer.